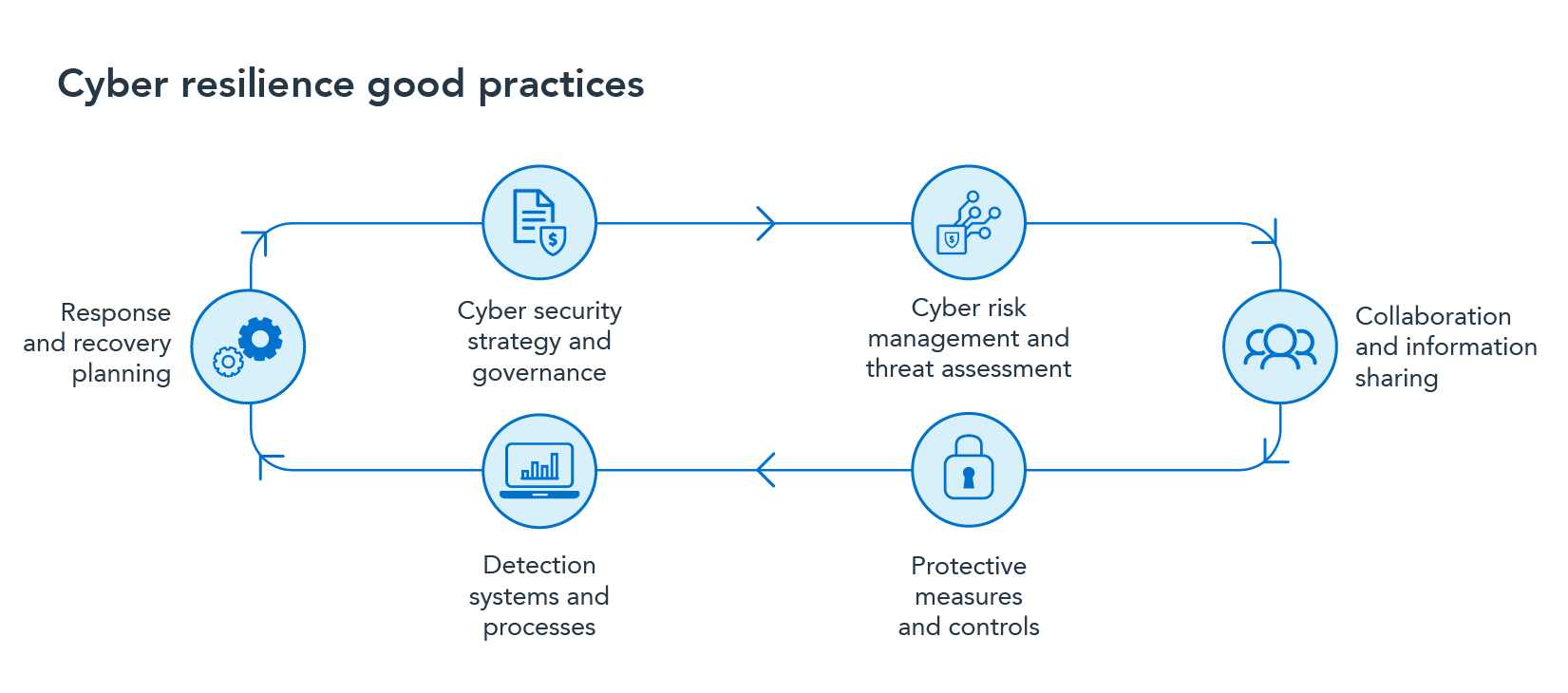
Cyber resilience good practices
Cyber resilience is vital to all businesses operating in the digital economy.
These good practices were identified as part of a previous self-assessment process by a sample of financial entities against the NIST Cybersecurity Framework, as well as more detailed follow-up discussions we conducted, see Report 468 Cyber resilience assessment report: ASX Group and Chi-X Australia Pty Ltd (REP 468).
Cyber security strategy and governance
The good practices we observed in relation to cyber security strategy and governance were characterised by board ‘ownership’, and responsive and agile governance models.
Board engagement
Periodic review
Boards take ownership of cyber strategy and ensure it is reviewed on a periodic basis to assess progress against success measures outlined in the strategy. Measures include time to detection, speed of response and recovery process.
Cyber resilience as a management tool
The management of cyber resilience is viewed by the board as a critical management tool for understanding risk status and making important investment decisions on cyber risk. It is seen as a tool for ‘enabling’ (not limiting) the organisation—by anticipating scenarios and building protection against them to take advantage of market opportunities.
Cyber resilience fluency
Board members are becoming increasingly educated in the language of cyber resilience and the potential threats to organisations and are more readily able to ask risk and audit committees the relevant questions. This reflects an active understanding of the cyber threat landscape and the planning and testing of response scenarios. See our Key questions for Boards.
Assurance processes
Assurance processes are focused on end-to-end business processes. This is undertaken with a view to confirming that critical business operations, technology applications and infrastructure, and the supporting data, are tested as a whole rather than independently of business processes and technology functions. This will ensure that critical business processes can be re-activated if and when an incident occurs.
Governance
Responsive governance
Businesses are tailoring traditional governance processes, to ensure ‘responsive governance’. In a rapidly changing cyber risk environment, the policies and procedures of today are not necessarily valid for long periods of time, and may not remain valid between typical annual review cycles.
This approach considers how adjustments can be driven by events and incidents, rather than by keeping to a fixed review period – which might result in needed changes being delayed until the next periodic review period.
Alignment with the organisation's overall governance framework
Cyber security governance is clearly and visibly aligned to other organisation-wide governance processes and procedures. This means that documented strategies, principles, policies, rules and procedures are in line with the overall governance framework.
Cyber risk management and threat assessment
Good practice in the area of cyber risk management and threat assessment is led by intelligence gathering through the use of third-party experts, and driven by routine threat assessments, including of relevant third parties.
Cyber risk management
Cyber risk management is increasingly becoming intelligence-led and moving to near real-time processes through automation and use of risk management tools that can integrate many sources of risk, including those from collaboration and information-sharing sources such as peers in the industry, police and government agencies.
‘Fusion’ centres
Some businesses have established specialist functions within their organisations to monitor and address risks in real time, often known as ‘fusion’ centres.
Third-party risk management
As outsourcing and cloud-based services become more prevalent, the reliance on third-party service providers and partners has become essential to the provision of products and services for many organisations.
Third-party risk management
Organisations have developed risk-based assessment methods and tools to ensure that third-party suppliers and partners are regularly assessed to guarantee compliance with required security standards. Some organisations are also using external service providers to carry out periodic assessments of partners and vendors.
Our conversations with industry
In the first half of 2022 ASIC met with industry and professional associations to understand how participants identified, managed and mitigated cyber security risk arising from their suppliers.
It was clear that supply chain cyber risk is complex and difficult to manage. Businesses need to be able to define their risk appetite and identify risks relevant to their organisation. This is critical to ensuring a business’ ability to put in place risk management mitigants appropriate to the nature, scale and complexity of their business.
Five common themes were identified. We encourage businesses to consider these themes in their risk management frameworks:
Finding your weakest link isn’t always easy
Most businesses were aware they were only as strong as the weakest link in their supply chain. However, they often faced difficulty obtaining visibility into their suppliers' operations.
Many businesses used contract terms to help increase transparency and mitigate fourth-party risk, for example, by requiring suppliers to notify the organisation if their subcontractors or vendors experienced a cyber security event.
However, in some cases, businesses felt they had limited bargaining power, for example, when negotiating contracts with larger, established third-party suppliers. This was common in sectors where there was reliance on a small number of vendors.
Innovation and cyber security can coexist
For most businesses, cyber security did not mean sacrificing innovation. Instead, it highlighted the need for robust vendor risk management practices. For example, businesses were able to effectively leverage innovation when they:
- viewed cyber risk through an enterprise lens, for example, by outsourcing in accordance with established risk appetite statements, and
- conducted periodic risk-based testing of the cyber security of their suppliers, for example, scenario testing and risk-based vendor assessment and testing.
People matter
Many businesses recognised their people were their greatest defence against cyber risk in the supply chain. For example:
- businesses that fostered close collaborative relationships with their suppliers rather than relying on contract terms obtained more timely threat intelligence
- businesses that empowered staff to actively consider cyber risk (e.g. through training and awareness or integration of cyber expertise in the business) helped minimise exposure to cyber threats.
We need to speak the same language
Management of cyber security risk is not just the domain of the IT department or a supplier of IT services.
Businesses that tackled the initial 'barrier of ignorance' and made cyber literacy a priority were better placed to identify, manage, and mitigate cyber risk in the supply chain.
The right information at the right time
A key concern for decision-makers was that they were not getting the right information at the right time to make informed decisions.
Many decision-makers were actively seeking opportunities to uplift their own capabilities. However, reports were often too complex or jargon-heavy, making it hard for decision-makers to understand the cyber risks facing their organisation.
We heard that:
- having an independent audit or assessment of their organisations' cyber resilience helped them make informed risk decisions
- having board members and/or senior management with information technology competency changes the nature of the conversations around cyber security.
Collaboration and information sharing
Collaboration is often characterised by confidential information-sharing arrangements with other financial institutions, security agencies and law enforcement. Information sharing is fundamental for organisations that are intelligence-led and aids in understanding attackers and potential threats, including terrorist organisations, political activists, organised crime and nation-state-sponsored attackers. This process also helps organisations to understand attackers’ motives—whether it be information, funds or general disruption.
Collaboration and information sharing
To gather intelligence, businesses are often engaging specialist third-party providers to undertake security monitoring and assessments. By employing the services of specialist individuals and companies operating in foreign jurisdictions, businesses are able to gather threat intelligence.
Businesses also have confidential information-sharing arrangements in place with other financial institutions, security agencies and law enforcement.
Asset management
Effective management of organisational assets is characterised by centralised management systems for critical internal and external assets (e.g. software and data), and configuration management that ensures visibility of critical assets.
Asset management
Centralised asset management system
Asset inventories for hardware, software and data, both internal and external to organisations, are managed through a centralised asset management system.
Configuration management
Configuration management is important for ensuring there is visibility of critical assets across the organisation, and for managing software versions and security patches.
Cyber awareness and training
There is clear recognition that effective cyber resilience requires a strong ‘cultural’ focus driven by the board and reflected in organisation-wide programs for staff awareness, education and random testing, including of third parties.
Training
Development of organisation-wide programs and strategies to ensure staff awareness and education—including for contractors and partners—which is effectively managed and monitored against success criteria.
Continuous development
Strategies based on a program of continuous development of knowledge and awareness—so that, through active vigilance, staff become an effective defence against malicious cyber activities by preventing incidents arising from attempted phishing attacks and other forms of social engineering.
Random staff testing
Random testing of staff enables the organisation to measure the effectiveness of cyber awareness programs (e.g. a test email containing malware is sent to a staff member or group to test their response) and to take appropriate measures based on the response (i.e. staff may be required to undertake further training if they do not manage the situation in accordance with their training).
Protective measures and controls
Proactive measures and controls for cyber risks are characterised by the implementation of the Australian Signals Directorate’s (ASD) strategies for mitigating targeted cyber intrusions (or equivalent), as well as a range of additional controls (e.g. encryption for ‘data in transit’ based on a risk assessment of the asset in question).
Protective measures and controls
Businesses have already implemented or have made it a priority to implement the ASD's ‘Essential Eight' strategies to mitigate targeted cyber incidents. This is accompanied by the 'essential eight maturity model' which enables organisations to self-assess their relative maturity against the essential eight recommendations.
Additionally, the more progressive organisations have also sought to apply:
- security as an integral part of their systems development lifecycle, sometimes known as the Security Development Lifecycle (SDL)
- encryption for stored data and ‘data in transit’ based on a risk assessment of the assets in question
- filtering and monitoring of outbound email messages to ensure that data is not transmitted outside of the organisation’s network in error or through intent, and
- highly restricted access to use of USB ports on computer equipment to minimise risks of data leakage or introduction of unauthorised software or files.
Detection systems and processes
There has been a lot of development in the approaches taken by ‘good-practice’ organisations in the area of cyber detection systems and processes. Good practices are characterised by the use of enterprise-wide continuous monitoring systems and the use of data analytics to integrate sources of threats in real-time.
Detection systems and processes
Continuous monitoring systems
Continuous monitoring systems, often organisation-wide, are implemented to monitor events on the organisation's network and systems using Security Information and Event Management (SIEM) technologies. SIEM technologies enable the detection and alert of anomalous user behaviours such as access to applications or files, as well as abnormal movement of information across the networks measured against a baseline reference of ‘normal’ activity.
Data analytics
Organisations are using data analytics to enable them to integrate sources of threats and associated risks into a single view of the threat landscape in real-time. Threats detected by the organisation, in addition to information collected through collaboration and information-sharing channels, are analysed to move response capability towards predicting malicious cyber activities.
‘Red teaming’
Employing technical specialists to work on breaking into an organisation’s networks.
Response and recovery planning
Response planning for cyber risks is different from standard business continuity planning because the scenarios are not as predictable, in part due to:
- the range of threat sources, and
- the speed at which the sophistication levels of attacks are changing.
Good practices we observed included routine and detailed scenario planning, war gaming, proactive reporting to the board and well-developed communication plans.
Response planning
Organisations are adopting some of the following practices:
- Scenario planning: To predict the types of incidents that may occur based on their specific risk profile, and implementing and exercising response processes.
- War gaming: Some organisations are using war gaming techniques to better understand and plan their defence against malicious cyber activities.
- Proactive reporting to the board: Reporting of changing threats and the counter measures that are in place.
Recovery planning
In the event of a data breach, organisations have actively determined when and how to notify customers—and there is a well-defined communication plan in place for managing stakeholders and public relations.